Telecommunications Denial of Service (TDoS) Protection
Telecommunications Denial of Service (TDoS) attacks pose a significant threat to communication infrastructures, aiming to disrupt services by overwhelming systems with excessive traffic. Effective TDOS protection is essential to ensure uninterrupted service and maintain the integrity of your telecommunications systems.
Features Overview
The system monitors incoming calls and applies configurable thresholds to detect and temporarily block suspicious calling patterns.
TDoS protection policies protects your business and mitigate denial of service attacks in real-time. Key features include:
- Rate Limiting per Policy: Configure specific rate limits to control the number of calls within a defined time window, preventing overloads.
- Attack Behavior Detection: Identify and block malicious actors exhibiting aggressive calling patterns without recording individual numbers.
- Temporary Blocking Mechanism: Automatically block offending numbers for a short duration, reducing the risk of prolonged disruptions.
- Customizable Thresholds: Set call thresholds, time windows, and expiration times to adapt to changing traffic patterns and threat levels.
Feature Requirements
- Call Telemetry Server Appliance 0.8.4 or later
- Call Telemetry Advanced License
- Cisco Callmanager 8.5 Integration Recommended
- CURRI or XCC Integration with Call Telemetry
TDOS Detection and Blocking Process
Implementing TDOS protection involves setting up call policies that monitor call traffic and enforce rate limits based on defined parameters. Here's how to configure and manage TDOS protection:
Configuring Rate Limits
-
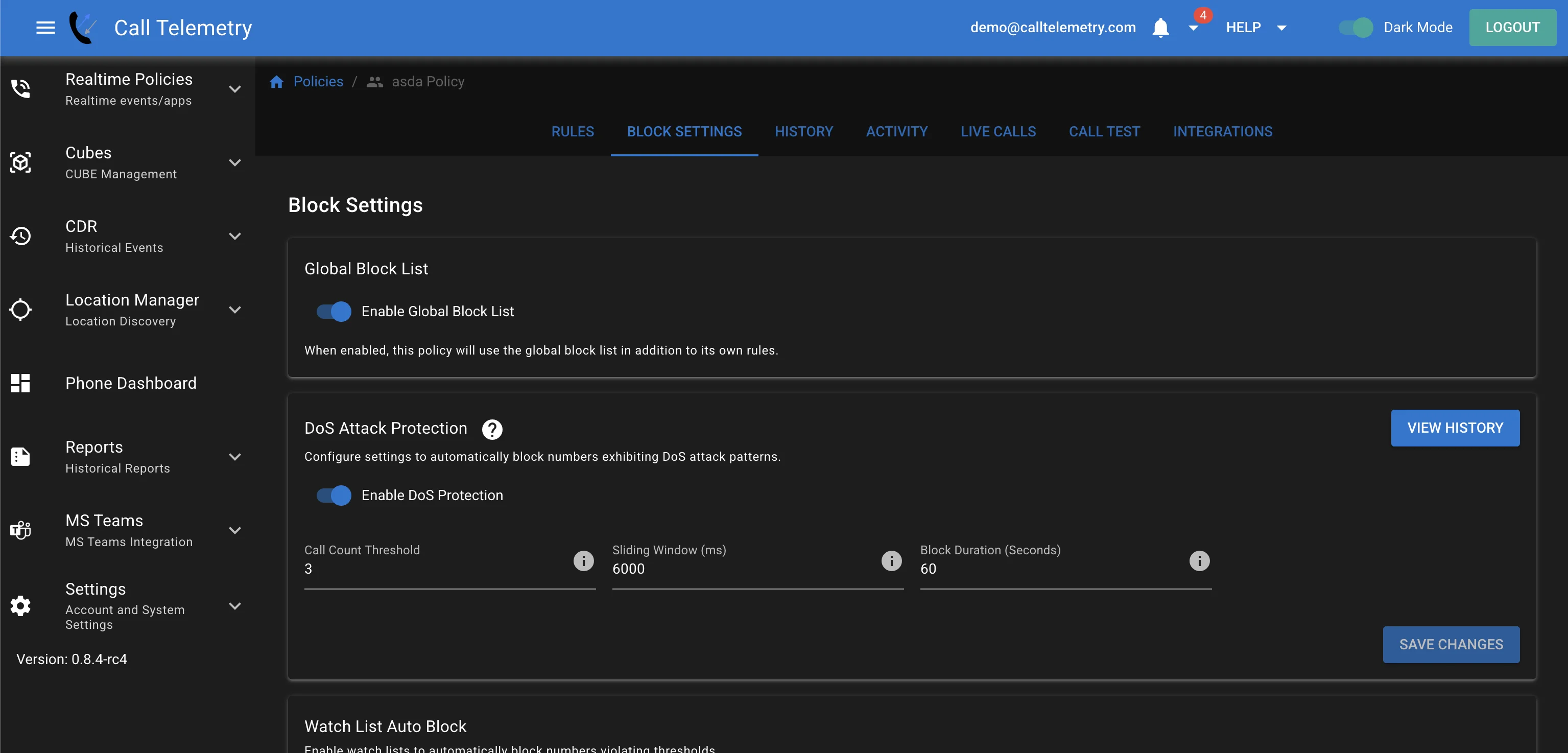
Enable TDoS Protection:
- Ensure that DOS Attack Protection is enabled on your Call Telemetry policy.
-
Access TDoS Protection Settings:
- Navigate to Settings -> Block Settings -> TDoS Protection in your Call Telemetry appliance.
-
Set Call Thresholds:
- Define the maximum number of calls (e.g., 50 calls) allowed within a specific time window (e.g., 30 seconds).
-
Set Block Expiration Time:
- Specify the duration (e.g., 5 minutes) for which offending numbers will be temporarily blocked.
-
Save Changes:
- Save the configuration to activate the TDOS protection on the policy.
Settings Page Screenshot
Monitoring TDoS Violations
Once TDoS protection is enabled, the system will automatically monitor incoming calls and apply the configured thresholds. If a number exceeds the defined limits, it will be temporarily blocked for the specified duration.
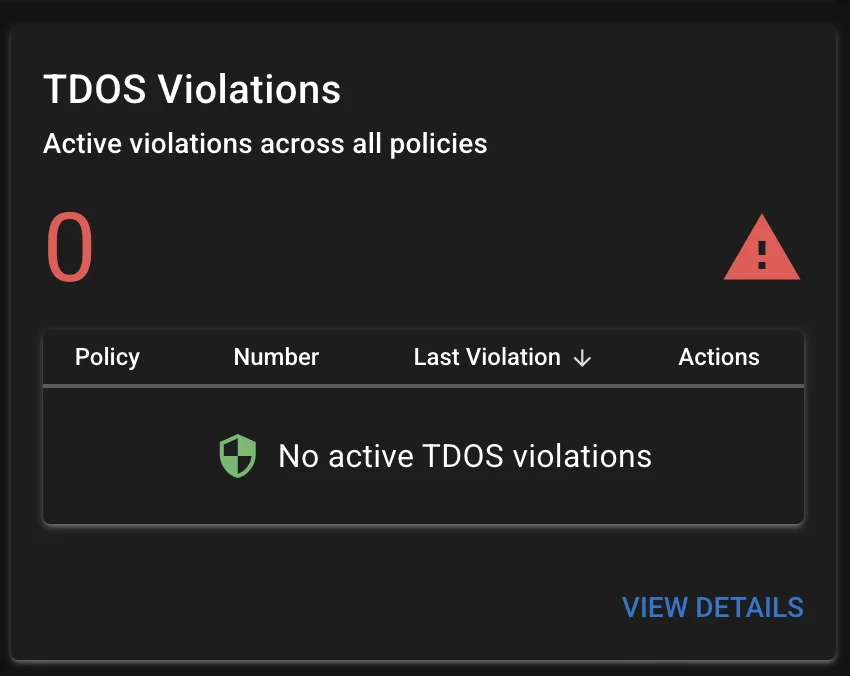
You can see the active TDoS violations in the Dashboard under TDoS Violations. The card section provides a summary of blocked numbers, including the number of calls and the time of the violation.
Dashboard Screenshot
Historical TDoS Violations
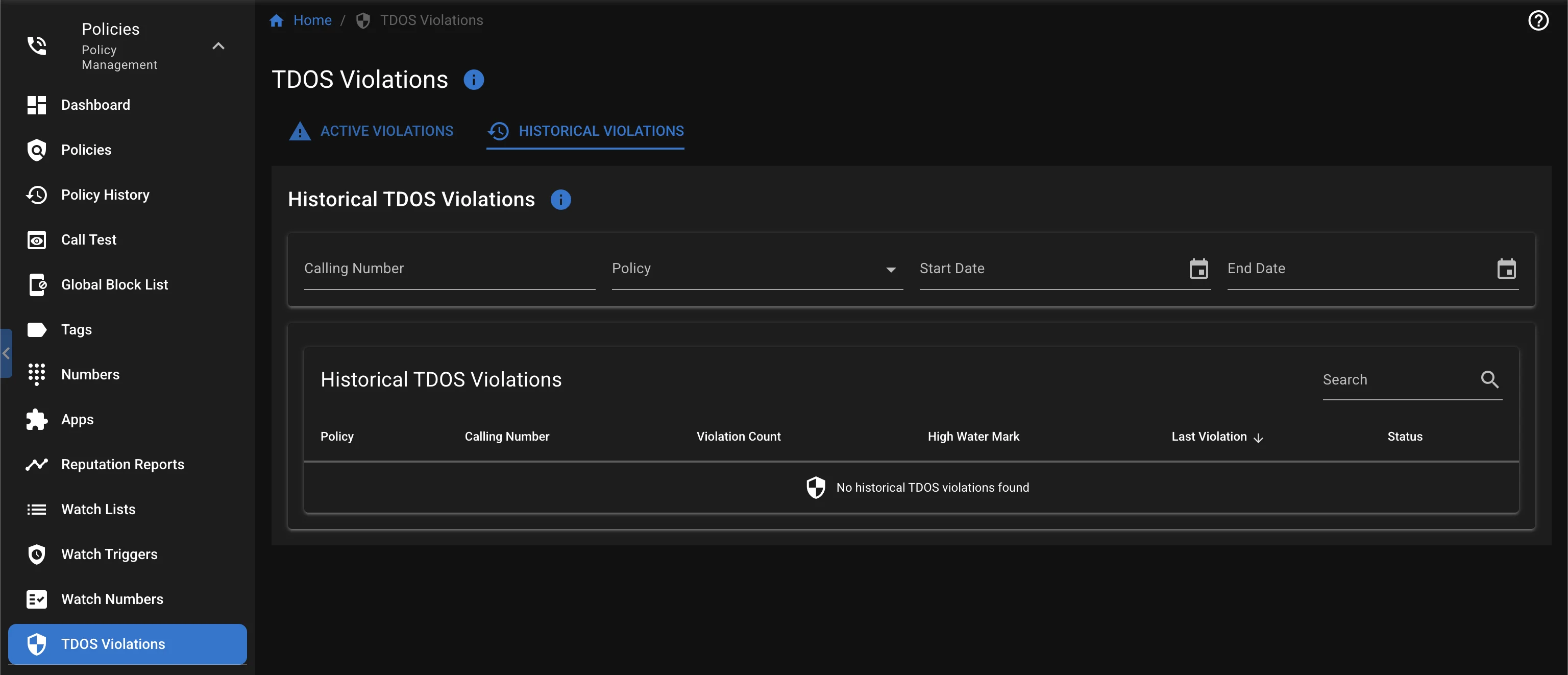
To view historical TDoS violations, you can press the View History button on the TDoS Dashboard card. This will take you the TDoS Violations page, where you can see both active and historical TDoS violations, including the number of calls, time of violation, and the high water mark of calls.
Alarms and Notifications
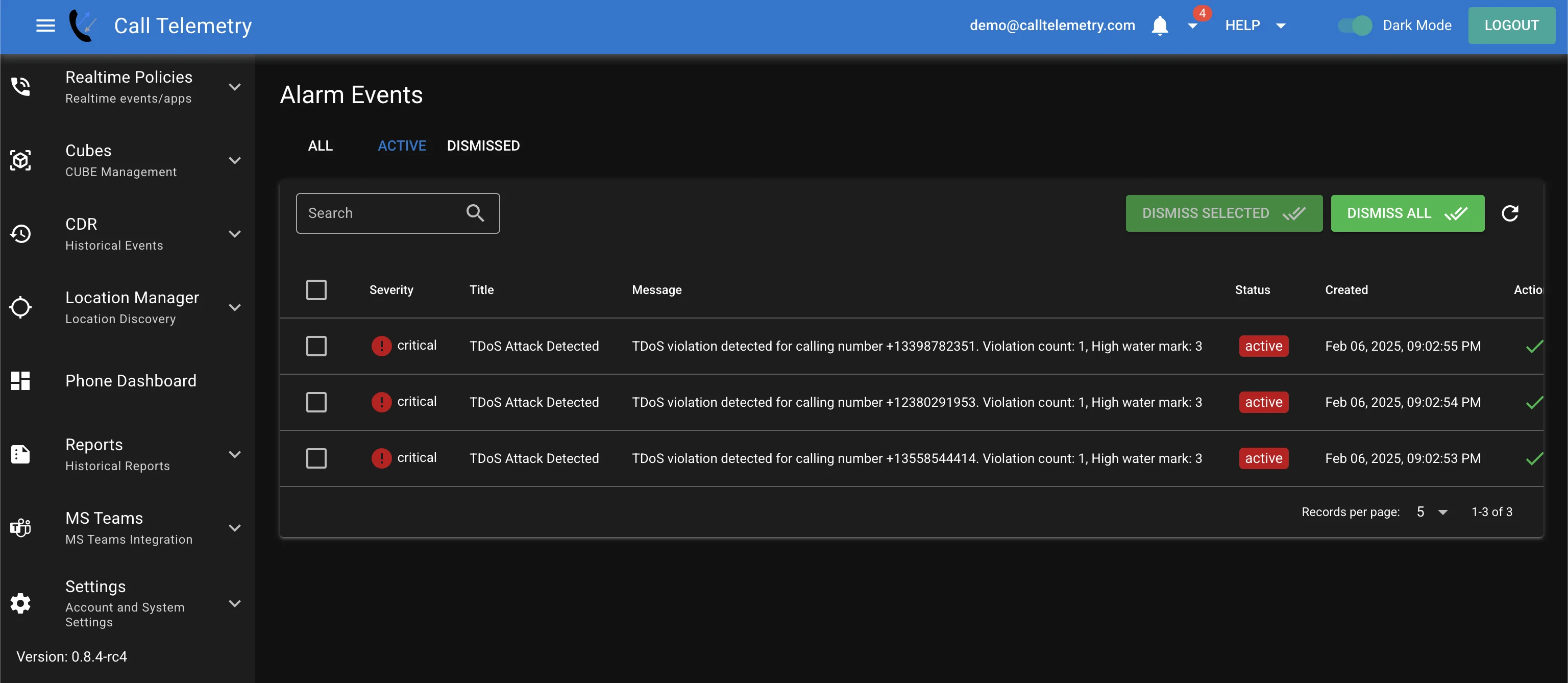
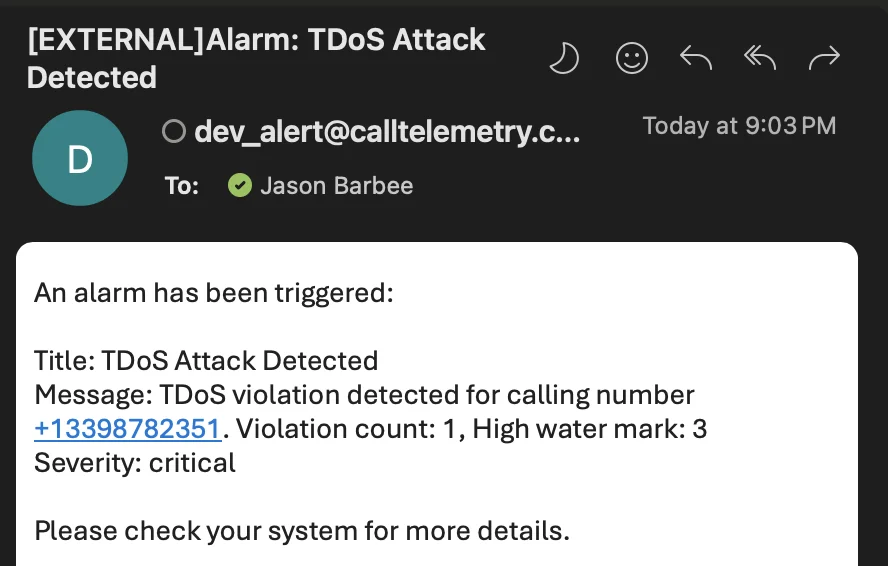
Administrators will receive email notifications when TDoS protection is triggered, providing real-time alerts for immediate response. Active and historical alarms are shown in the Dashboard
Sample Alarms
Key Differences between TDoS Protection and Watch Lists
TDoS Protection and Watch Lists serve complementary but distinct security purposes:
-
TDoS focuses on immediate threat response, automatically blocking aggressive calling patterns for short periods. It's designed to mitigate active attacks without requiring manual intervention. TDoS violations are stored historically, but are not added to watch lists, or the global block list.
-
Watch Lists enable longer-term monitoring and analysis of suspicious behavior. You can monitor suspicious call activity over time based on thresholds. Adminstrators can review, comment on them, whitelist or block them based on findings.
TDoS vs Watch Lists Comparison
| Feature | TDoS Protection | Watch Lists |
|---|---|---|
| Time Frame | Short-term (seconds/minutes) | Long-term (minutes/hours) |
| Use Case | Immediate attack mitigation | Pattern analysis & monitoring |
| Configuration | Simple rate limits | Complex trigger conditions |
| Block Duration | Temporary (minutes) | Extended (days to permanent) |
| Management | Automated | Manual Review / Automated |
When to Use Each
Use TDOS Protection when:
- You need immediate response to aggressive calling patterns
- Dealing with active DOS attacks
- Automated protection is required
Use Watch Lists when:
- Investigating suspicious patterns over time
- Documenting and reviewing call activity
- Need flexible management of blocked numbers
- Want to maintain an audit trail of actions taken