Appearance
Blocking Unwanted Calls with Call Telemetry
Call Telemetry provides a comprehensive set of tools to protect your organization from unwanted, spam, and malicious calls. This guide will walk you through the features and options available to you.
Centralized Voice Security and Call Blocking
Call Telemetry brings together multiple integration points of call blocking intelligence via CURRI and XCC into a single, centralized policy enforcement system. This ensures consistent protection across your entire voice infrastructure.
How Policies Are Enforced
Once centralized in Call Telemetry, these policies are enforced at two key points in your voice infrastructure:
Two Ways to Integrate with Your Cisco Infrastructure
Call Telemetry offers two integration methods:
| Feature | CURRI (CUCM) Integration | XCC (CUBE) Integration |
|---|---|---|
| Enforcement Point | Cisco Callmanager | Cisco CUBE routers |
| Diaplan Scope | Enterprise Internal | PSTN Network edge |
| Applied to | Route and Translation patterns or extensions | All traffic through CUBE |
| Best For | General Purpose Policy Control | Network-edge protection |
| Setup Complexity | Simple integration, granular application | Easy network-edge setup |
You can use either integration method independently or combine them for comprehensive protection at both the network edge and within your call processing.
Sources of Call Blocks
Call Telemetry provides multiple ways to block unwanted calls, giving you a comprehensive defense against spam, robocalls, and malicious callers:
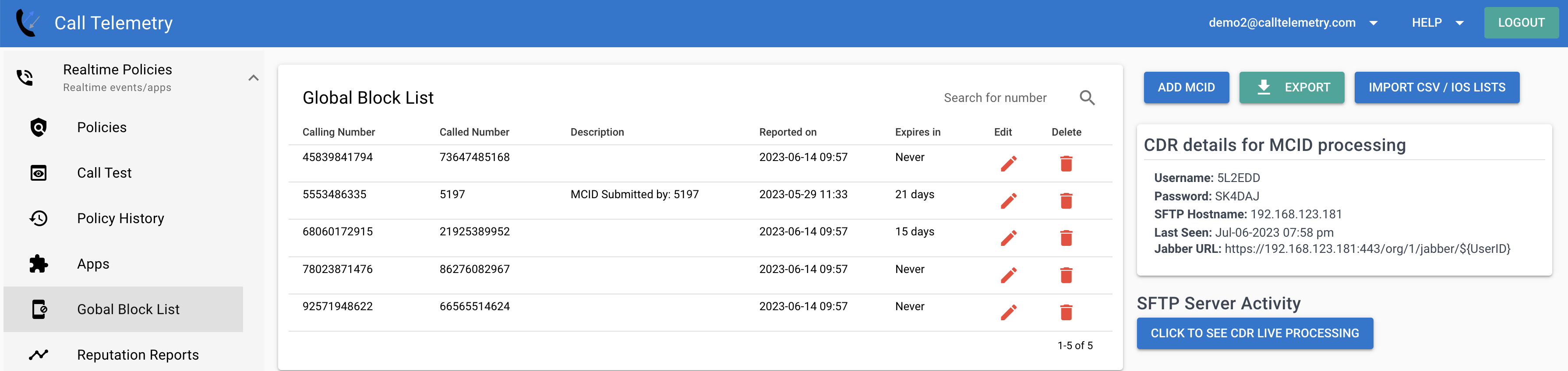
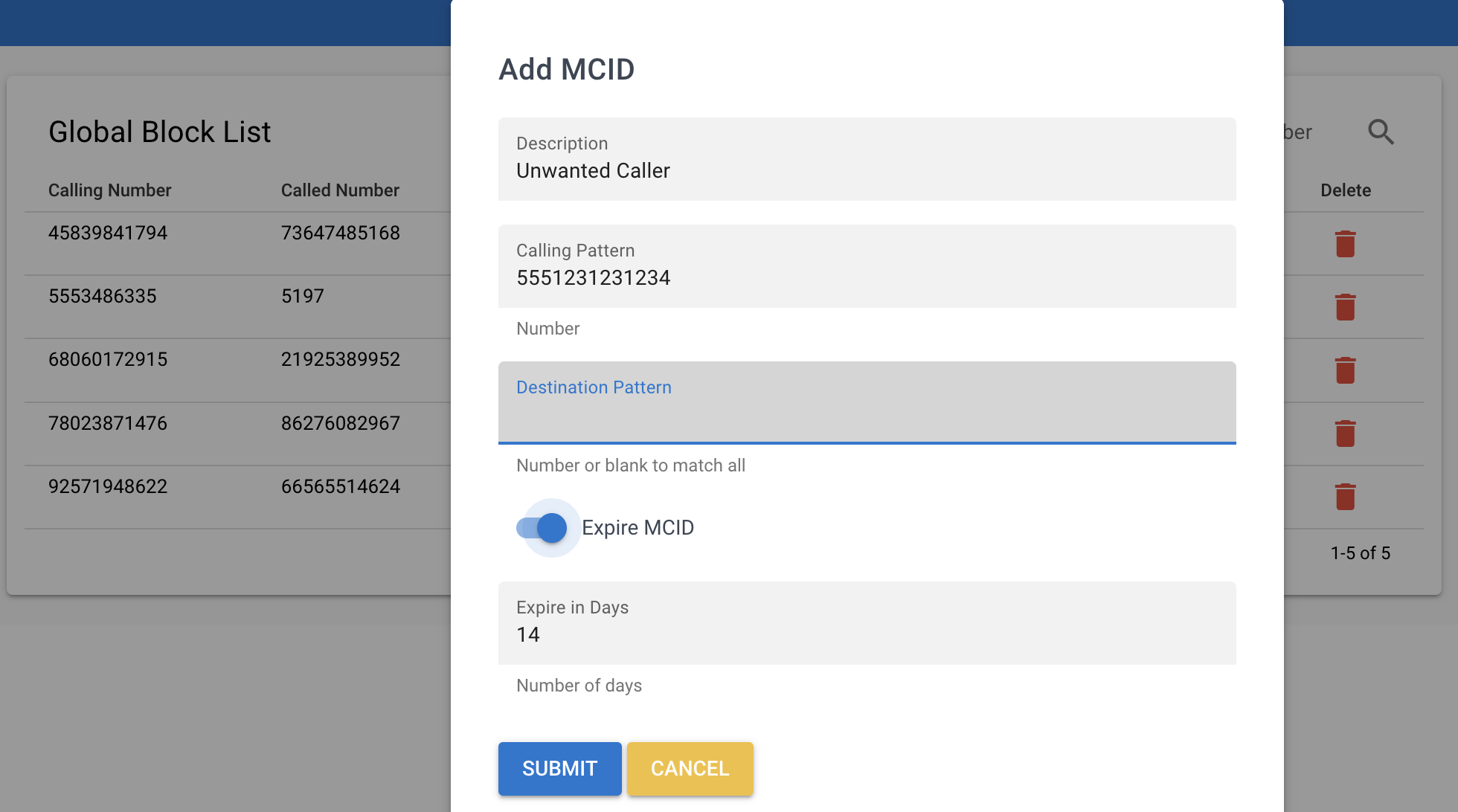
1. Administrator-Managed Blocks
Administrators can directly manage the Global Block Call Table through the web interface or API:
- Add individual numbers or ranges
- Import block lists from CSV files
- Set automatic expiration dates for temporary blocks
- Add notes and reasons for blocks
2. User Self-Service Blocks
Empower your users to block unwanted calls themselves:
- Cisco IP Phone MCID Button: Users can tag unwanted calls using the Malicious Call ID (MCID) softkey
- Cisco IP Phone XML Service: Web portal accessible directly from IP phones
- Cisco Jabber Portal: Custom embedded tab in Jabber for call blocking
- User-specific blocks: Each user manages their own block list
3. Automated Protection Systems
Intelligent systems that automatically detect and block suspicious call patterns:
- TDoS Protection: Automatically blocks aggressive calling patterns that could indicate a Telecommunications Denial of Service attack
- Watch Lists & Triggers: Monitors for suspicious call activity based on thresholds and adds numbers to watch lists for review
- Reputation-Based Filtering: Routes calls based on TrueSpam reputation scores
4. API Integration
Integrate call blocking with your existing systems:
- Full REST API access to the block list
- Automated call blocking scripts
- Integration with security systems and other platforms
Centralized Block List Management
The Global Block Call Table simplifies administration across your entire voice infrastructure:
Key Benefits Over Native Cisco Solutions
Traditional Cisco call blocking methods have several limitations:
- Cisco IOS Reject Rules: Limited to 100 rules, not centrally managed
- Transformation Patterns: Require complex CSS/Partition planning, can't sync across clusters
- End User Management: Users typically must call helpdesk to block calls
- No Centralized Policy: Difficult to manage large block lists or integrate with other systems
- No Expiration Options: No way to automatically expire blocks
- Carrier Retry Issues: Some carriers retry rejected calls, consuming more resources
How Call Telemetry Solves These Challenges
- Centralized Management: Single interface for all blocks, even across clusters
- Multiple Integration Points: Works with both CURRI and XCC
- Self-Service Options: Users can submit their own blocks
- Expiring Blocks: Set time limits on blocked numbers
- Soft Blocks: Redirect calls instead of rejecting them
- Full API Access: Automate block list management
Intelligent Call Routing with Reputation Services
Beyond simple blocking, Call Telemetry can make intelligent routing decisions based on caller reputation:
TrueSpam Cloud Reputation
The TrueSpam Cloud Reputation App provides real-time reputation scores for incoming calls, allowing you to:
- Block Known Spam: Automatically block calls with poor reputation scores
- Rename Caller ID: Flag suspicious calls (e.g., "Potential Spam")
- Redirect Calls: Send suspicious calls to voicemail or another number
- Allow Known Good: Ensure important calls get through
Watch Lists and Triggers
Watch Lists and Triggers provide proactive protection:
- Threshold Monitoring: Set thresholds for suspicious call activity
- Automatic Detection: Add suspicious numbers to watch lists
- Administrator Review: Review, comment on, and take action on watched numbers
- Flexible Actions: Block, ignore, or monitor suspicious numbers
TDoS Attack Protection
TDoS Protection defends against Telecommunications Denial of Service attacks:
- Rate Limiting: Configure call rate limits to prevent system overload
- Automatic Blocking: Temporarily block aggressive calling patterns
- Real-time Alerts: Notify administrators of potential attacks
- Customizable Thresholds: Adapt to your organization's normal call patterns
Self-Service Call Block Portals
Empower your users to protect themselves from unwanted calls:
Blocking Calls from Cisco IP Phones
Users can block unwanted calls directly from their Cisco IP Phones using:
- MCID Button: Tag calls as malicious using the Cisco MCID softkey
- XML Service: Access a web portal directly from the phone
- User-Specific Blocks: Each user manages their own personal block list
- Expiring Blocks: Blocks can expire after a set period or be permanent
Blocking Calls from Cisco Jabber
Jabber users can block calls using:
- Jabber Custom Tab: Embedded web portal in Jabber
- Personal Block List: User-specific blocks across all devices
- Simple Interface: Easy-to-use block submission form
Call Block Management via API
For advanced integration and automation, Call Telemetry provides a comprehensive API that allows you to:
- Add, remove, and query blocked numbers
- Set expiration dates for blocks
- Integrate with other security systems
- Create custom block list management tools
- Automate responses to security incidents